What Is Hashing What Is Hashing With Example Hashing Explained Simply Simplilearn
What Is A Hash Hacking Tutorials By Xeus 🔥mit post graduate program in cyber security simplilearn pgp cyber security certification training course?utm campaign=jmtzx npfdc&utm. Omar bheda. hashing is the practice of transforming a given key or string of characters into another value for the purpose of security. although the terms “hashing” and “encryption” may be used interchangeably, hashing is always used for the purposes of one way encryption, and hashed values are very difficult to decode.

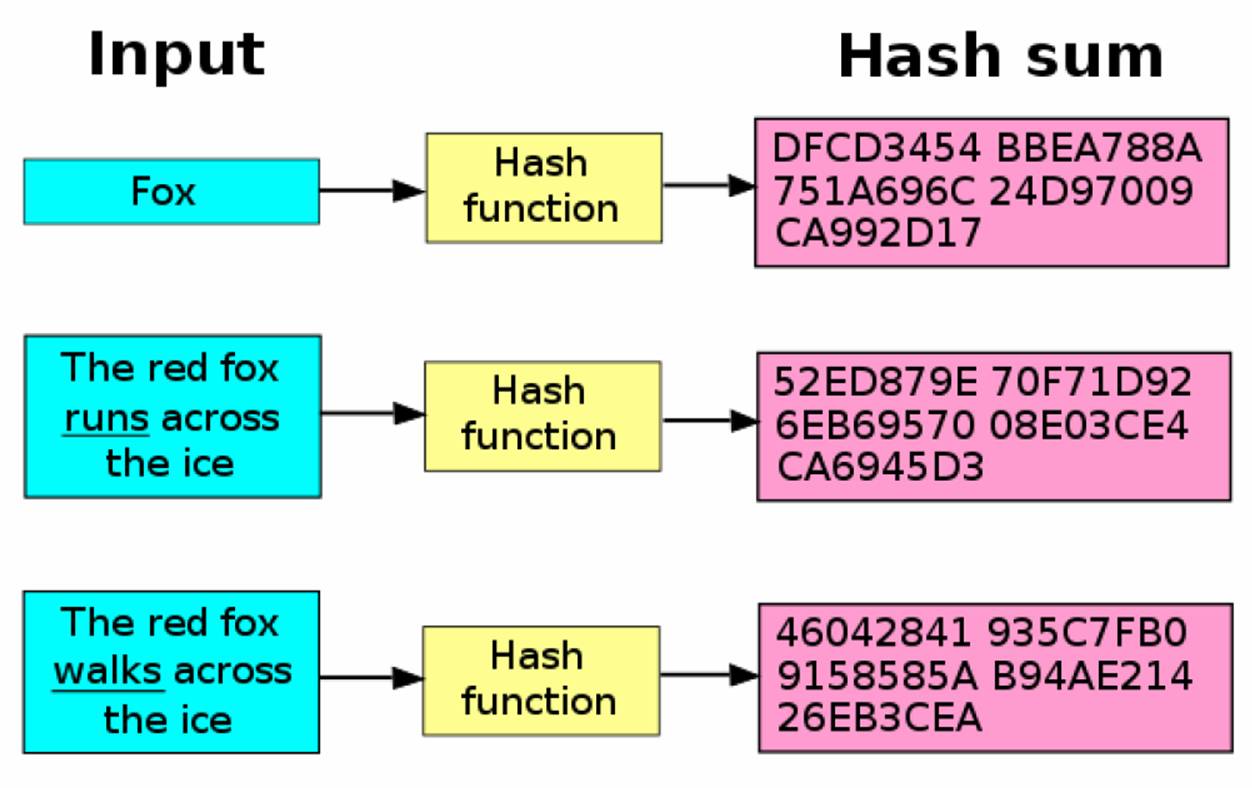
Hash Functions And Cryptography Web3 Encyclopedia In this presentation on what is hashing, we learn about what is hashing with an example, the different applications, advantages and ways to strengthen hashes. hash functions and hashing guidelines are also explained, and we take a look at how salting and peppering help reduce hash collisions to. Hashing is the process of converting data — text, numbers, files, or anything, really — into a fixed length string of letters and numbers. data is converted into these fixed length strings, or hash values, by using a special algorithm called a hash function. for example, a hash function that creates 32 character hash values will always turn. Introduction to hashing. hashing is designed to solve the problem of needing to efficiently find or store an item in a collection. for example, if we have a list of 10,000 words of english and we want to check if a given word is in the list, it would be inefficient to successively compare the word with all 10,000 items until we find a match. Hashing is the process of transforming any given key or a string of characters into another value. this is usually represented by a shorter, fixed length value or key that represents and makes it easier to find or employ the original string. the most popular use of hashing is for setting up hash tables. a hash table stores key and value pairs.
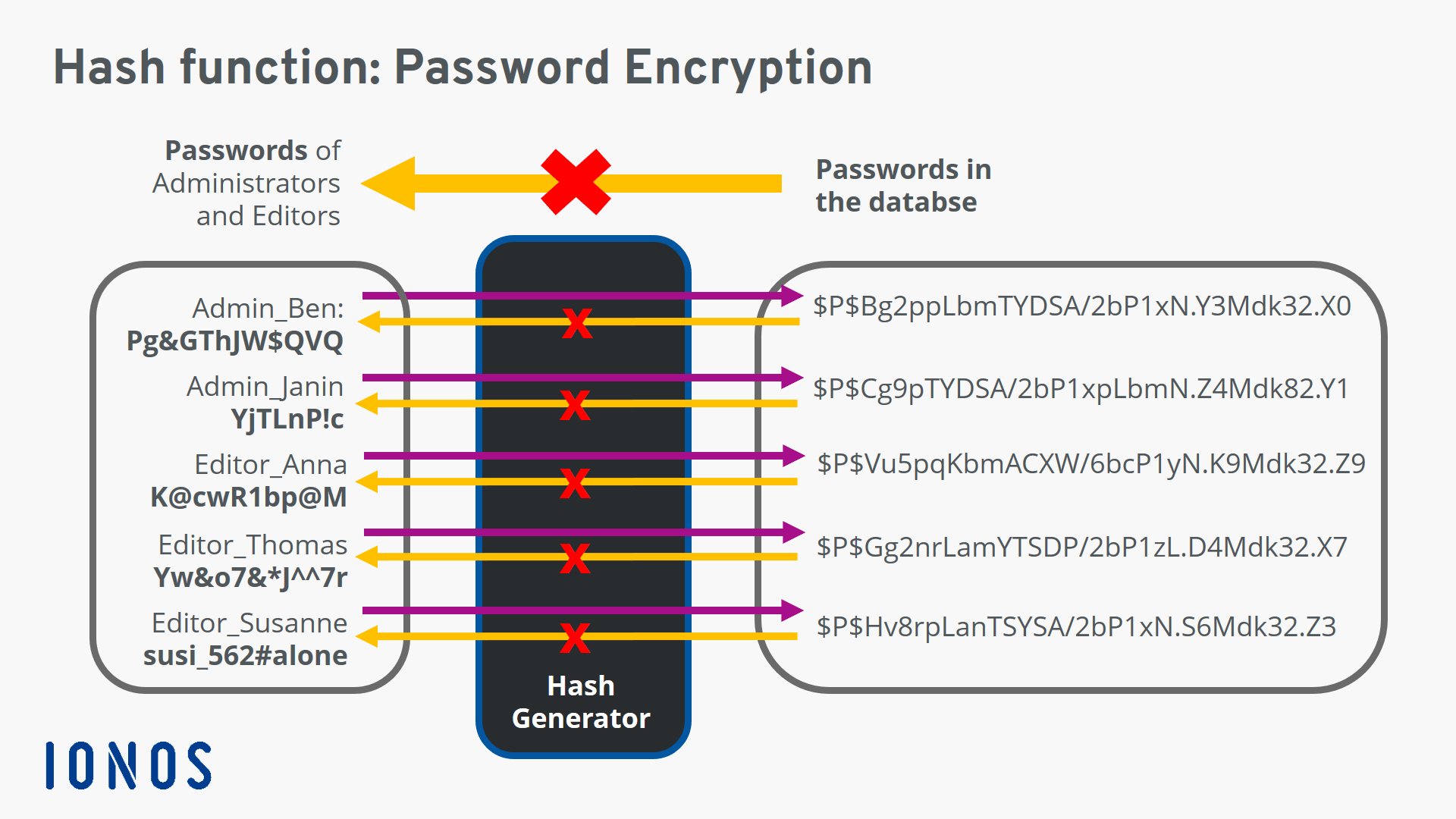
What Is A Hash Total Introduction to hashing. hashing is designed to solve the problem of needing to efficiently find or store an item in a collection. for example, if we have a list of 10,000 words of english and we want to check if a given word is in the list, it would be inefficient to successively compare the word with all 10,000 items until we find a match. Hashing is the process of transforming any given key or a string of characters into another value. this is usually represented by a shorter, fixed length value or key that represents and makes it easier to find or employ the original string. the most popular use of hashing is for setting up hash tables. a hash table stores key and value pairs. Hashing is an encryption technique used in cybersecurity to protect and manage information. learn more about what hashing is and how it’s used. hashing is a data security technique used to convert data values into alternate, unique identifiers called hashes for quick and secure access. hashing can be used for data security because the one way. Hashes are the output of a hashing algorithm like md5 (message digest 5) or sha (secure hash algorithm). these algorithms essentially aim to produce a unique, fixed length string – the hash value, or “message digest” – for any given piece of data or “message”. as every file on a computer is, ultimately, just data that can be.

Cryptographic Hash Function Youtube Hashing is an encryption technique used in cybersecurity to protect and manage information. learn more about what hashing is and how it’s used. hashing is a data security technique used to convert data values into alternate, unique identifiers called hashes for quick and secure access. hashing can be used for data security because the one way. Hashes are the output of a hashing algorithm like md5 (message digest 5) or sha (secure hash algorithm). these algorithms essentially aim to produce a unique, fixed length string – the hash value, or “message digest” – for any given piece of data or “message”. as every file on a computer is, ultimately, just data that can be.

Decoded Examples Of How Hashing Algorithms Work Dzone

Comments are closed.