What Is Hash Function Within Cryptography Quick Guide Positiwise
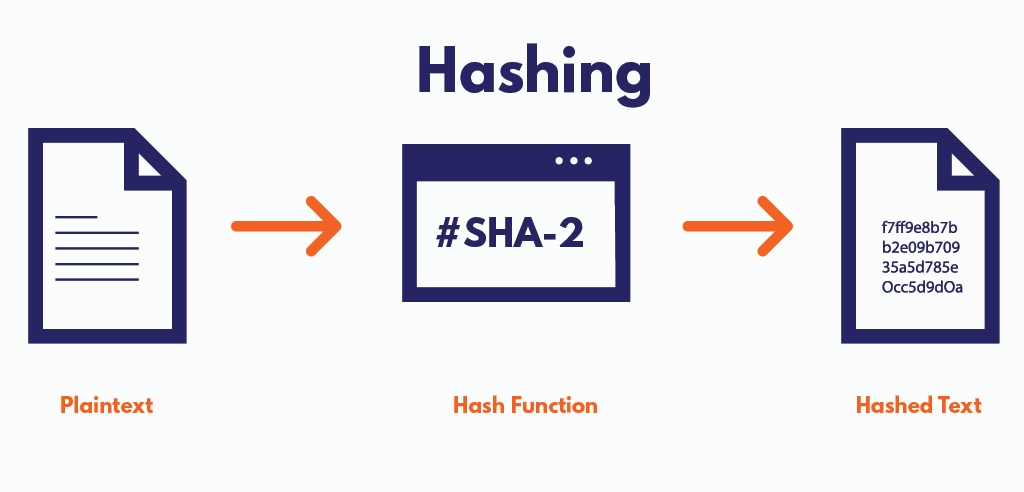
What Is Hash Function Within Cryptography Quick Guide Positiwise Put simply, the hash function is the mathematical process that has an essential part in public key cryptography. in addition, the hash function helps in: furthermore, these are helpful in many other ways. for instance, it helps sign software applications and secure the website connection to transmit information online. What is cryptography hash function? a cryptographic hash function (chf) is an equation that is widely used to verify the validity of data. it has many applications, particularly in information security (e.g. user authentication). a chf translates data of various lengths of the message into a fixed size numerical string the hash.

What Is A юааhashюаб юааfunctionюаб In юааcryptographyюаб A Beginnerтащs юааguideюаб Hashed Out By T A cryptographic hash function that produces 512 bit hash values. it is known for its resistance against various attacks and is commonly used in secure applications. these hashing algorithms, combined with the core functionality of hash functions, provide a robust foundation for ensuring data security and integrity in modern cryptography. A hash function is a one way mapping that takes an input m of variable length and produces a fixed length output h: h = h (m), where h (.) is the hash function. there are three different. 12.1: defining security. superficially, it seems like we have already given the formal definition of security: a hash function h is collision resistant if no polynomial time algorithm can output a collision under h. unfortunately, this definition is impossible to achieve! fix your favorite hash function h. Step 2: next, you feed your data into the function. this could be anything—a password, a document, or even an entire software program. your data is the ingredient in your hash recipe. step 3: the function then chops up your data, mixes it around, and cooks it up into a hash.

Comments are closed.