What Is A Hash Hacking Tutorials By Xeus
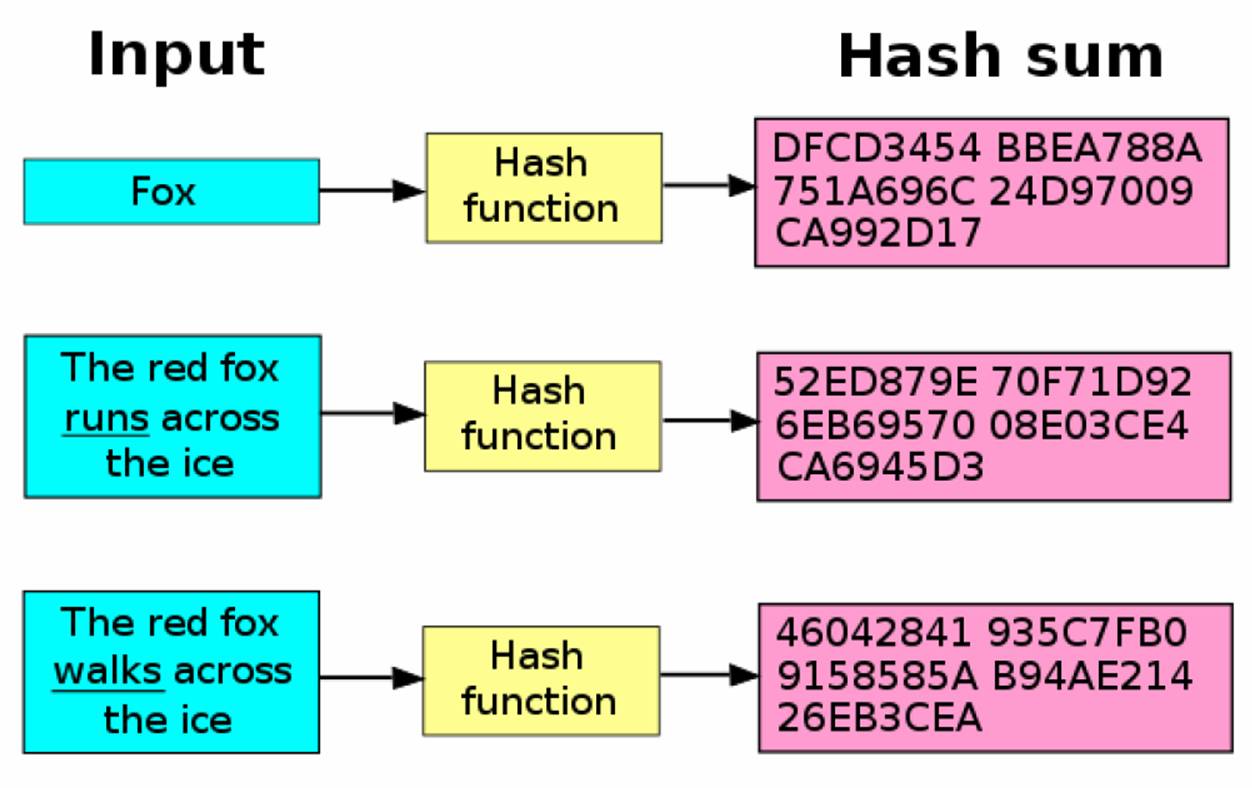
What Is A Hash Hacking Tutorials By Xeus Hashes are a way of taking any amount of data, jumbling it around, then shrinking the result to a fixed size output, a fingerprint. a cryptographic hash function or algorithm takes in an arbitrary block of data and returns a fixed length hash, such that any accidental or intentional change to the data will, with very high probability, change. Hacking tutorials by xeus a ray of hope in dark times. 11. apr. how quantum computing will turn digital security upside down what is a hash? this will make you high.

What Is A Hash Hacking Tutorials By Xeus Doxing: discovering and publishing the identity of an otherwise anonymous internet user by tracing their online publically available accounts, metadata, and documents like email accounts, as well as by hacking, stalking, and harassing. hash: a hash is a string or number generated by an algorithm from an input like a message or file. in a. A hash function might process a large dataset or file thousands or even hundreds of thousands of times before it generates the final hash value. this is why hashing algorithms need to be efficient in order to be effective. the hash value. the final output of the hash function is the hash value, which ideally should be unique to each input. We will crack this hash using the dictionary mode. this is a simple attack where we provide a list of words (rockyou) from which hashcat will generate and compare hashes. we can specify the hash mode as “md5” using the value 0. but hashcat can also identify the hash type automatically for common hash algorithms. Tryhackme goes way beyond textbooks and focuses on fun interactive lessons that make you put theory into practice. you'll get an immersive learning experience with network simulations, intentionally vulnerable technology based on real world examples and more.

What Is A Hash Hacking Tutorials By Xeus We will crack this hash using the dictionary mode. this is a simple attack where we provide a list of words (rockyou) from which hashcat will generate and compare hashes. we can specify the hash mode as “md5” using the value 0. but hashcat can also identify the hash type automatically for common hash algorithms. Tryhackme goes way beyond textbooks and focuses on fun interactive lessons that make you put theory into practice. you'll get an immersive learning experience with network simulations, intentionally vulnerable technology based on real world examples and more. A hash function is a function that takes an input (or ‘message’) and returns a fixed size string of bytes. the output, typically a number, is called the hash code or hash value. the main purpose of a hash function is to efficiently map data of arbitrary size to fixed size values, which are often used as indexes in hash tables. Rules for disk i o 1. know thy malware. do explicitly document the “disk forensic footprint” that could be potentially created by various features of a binary tool on a remote target.
What Is A Hash Hacking Tutorials By Xeus A hash function is a function that takes an input (or ‘message’) and returns a fixed size string of bytes. the output, typically a number, is called the hash code or hash value. the main purpose of a hash function is to efficiently map data of arbitrary size to fixed size values, which are often used as indexes in hash tables. Rules for disk i o 1. know thy malware. do explicitly document the “disk forensic footprint” that could be potentially created by various features of a binary tool on a remote target.

Comments are closed.