Hash Function In Cryptography How Does It Work Infosec Insights

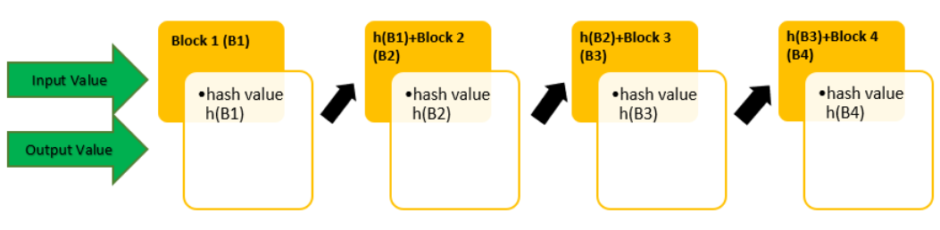
Hash Function In Cryptography How Does It Work Infosec Insights The process involved with a hash function in cryptography. in the graphic, the input value of data block 1 is (b1), and the hash value is h (b1). the next block 2’s input value b2 is combined with the previous hash value h (b1) to produce the hash value h (b2). this process of combining one block’s output value with the next block’s input. Infosec boot camps offer live, instructor led cybersecurity and it certification training in person or online. infosec self paced training accommodates your schedule with instructor guided, on demand training. infosec immersive boot camps kickstart cybersecurity careers with tailored training in as little as 26 weeks.

Hash Function In Cryptography How Does It Work Infosec Insights A hash function converts an input value of any arbitrary size to a fixed size value. thus, the input can be of any length but the output generated is always of a fixed length. the output generated is called hash values or hashes. one more important thing to be noted is hash functions and cryptography are altogether totally different from each. A definition and explanation. asymmetric encryption is a type of encryption that uses two separates yet mathematically related keys to encrypt and decrypt data. the public key encrypts data while its corresponding private key decrypts it. this is why it’s also known as public key encryption, public key cryptography, and asymmetric key. Hash functions play a central role in blockchain technology. each block in a blockchain contains a hash of the previous block, creating a secure and tamper evident chain of transactions. hash functions are also used for cryptographic security, address generation, and proof of work (mining) in blockchain networks. 8. Conclusions – the hashing function. for a primer article on cryptography, click here: dna cryptography and information security #gref. the disadvantages of symmetric key cryptography. although symmetric key cryptography does possess its advantages, it also has a set of disadvantages, which are as follows: key distribution; key storage and.
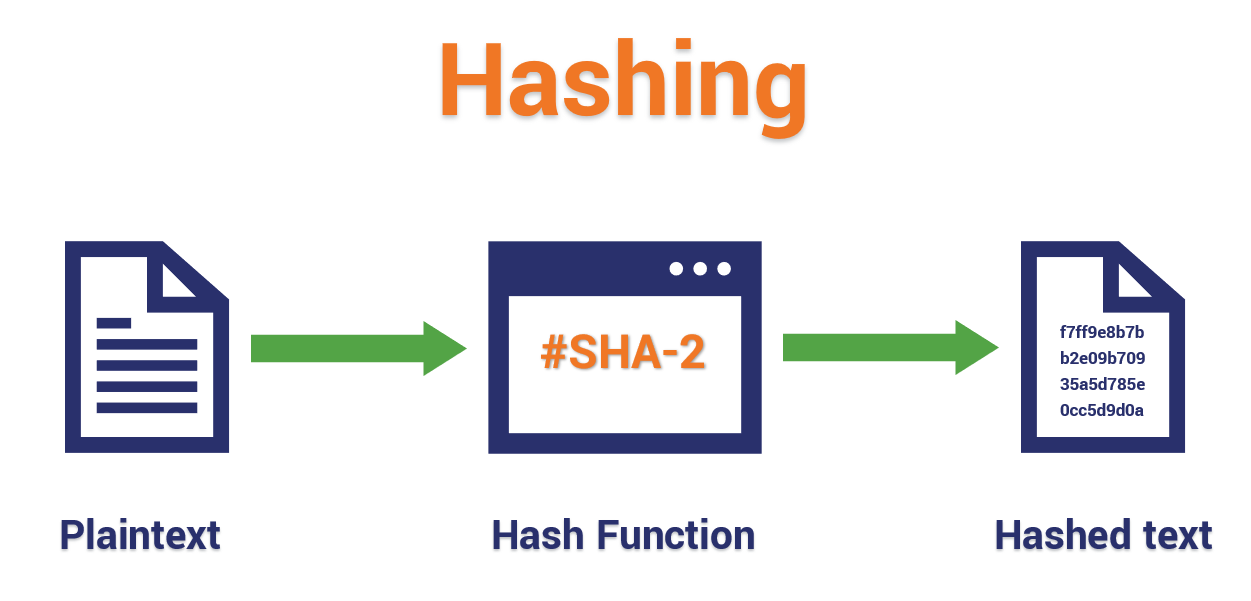
What Is A юааhashюаб юааfunctionюаб юааin Cryptographyюаб A Beginnerтащs Guide Hashed Out By The Ssl Hash functions play a central role in blockchain technology. each block in a blockchain contains a hash of the previous block, creating a secure and tamper evident chain of transactions. hash functions are also used for cryptographic security, address generation, and proof of work (mining) in blockchain networks. 8. Conclusions – the hashing function. for a primer article on cryptography, click here: dna cryptography and information security #gref. the disadvantages of symmetric key cryptography. although symmetric key cryptography does possess its advantages, it also has a set of disadvantages, which are as follows: key distribution; key storage and. Hashing is the process of converting data — text, numbers, files, or anything, really — into a fixed length string of letters and numbers. data is converted into these fixed length strings, or hash values, by using a special algorithm called a hash function. for example, a hash function that creates 32 character hash values will always turn. Note that a hash function is not an encryption function. encryption implies that you can decrypt (if you know the key). with a hash, there's no magical number that lets you go back. the main recommended cryptographic hash functions are sha 1 and the sha 2 family (which comes in several output sizes, mainly sha 256 and sha 512).
Hash Function In Cryptography How Does It Work Infosec Insights Hashing is the process of converting data — text, numbers, files, or anything, really — into a fixed length string of letters and numbers. data is converted into these fixed length strings, or hash values, by using a special algorithm called a hash function. for example, a hash function that creates 32 character hash values will always turn. Note that a hash function is not an encryption function. encryption implies that you can decrypt (if you know the key). with a hash, there's no magical number that lets you go back. the main recommended cryptographic hash functions are sha 1 and the sha 2 family (which comes in several output sizes, mainly sha 256 and sha 512).

Comments are closed.