5 Types Of Phishing Attacks And How To Avoid Them

5 Types Of Phishing Attacks And How To Avoid Them Unless the accounting department is hit — then a ridiculously high money transfer will likely make its way into a bank account on some paradise island! some of the most popular types of phishing attacks are spear phishing, vishing, smishing, whaling, https phishing and business email compromise (bec). Https phishing prevention tip: always look closely at the url of a site before logging in. 3. email phishing. one of the most common phishing attacks is email phishing. email phishing is when a cyberattacker sends you an email pretending to be someone else in hopes that you’ll reply with the information they requested.

The Major Types Of Phishing Attacks How To Identify Them The Definitive Guid Spear phishing: going after specific targets. phishing attacks get their name from the notion that fraudsters are fishing for random victims by using spoofed or fraudulent email as bait. spear. How to identify pop up phishing: irregularities: review for spelling errors or abnormal color schemes. shift to full screen mode: malicious pop ups can turn a browser to full screen mode so any automatic change in screen size might be an indicator. 10. clone phishing. The information you give helps fight scammers. if you got a phishing email, forward it to the anti phishing working group at [email protected]. (link sends email) . if you got a phishing text message, forward it to spam (7726). report the phishing attempt to the ftc at reportfraud.ftc.gov. Phishing attacks are a type of social engineering that aims to steal sensitive user information like usernames, passwords, credit card numbers, and bank account details. attackers impersonate a trusted entity to trick victims into opening an email, instant message, or a text message and clicking on a malicious link.
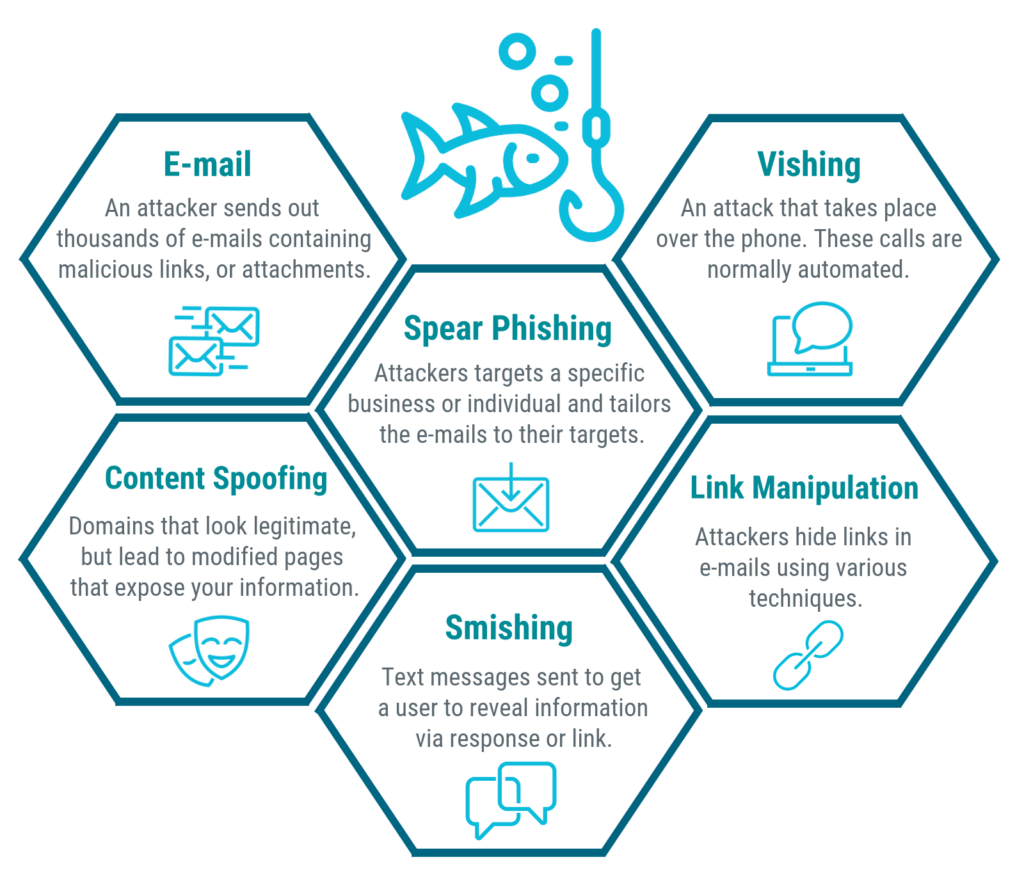
12 Types Of Phishing Attacks And How To Identify Them Bva Technology Service The information you give helps fight scammers. if you got a phishing email, forward it to the anti phishing working group at [email protected]. (link sends email) . if you got a phishing text message, forward it to spam (7726). report the phishing attempt to the ftc at reportfraud.ftc.gov. Phishing attacks are a type of social engineering that aims to steal sensitive user information like usernames, passwords, credit card numbers, and bank account details. attackers impersonate a trusted entity to trick victims into opening an email, instant message, or a text message and clicking on a malicious link. Regularly back up your data. routinely backing up your data is a good way to increase your peace of mind and help protect against the damage of phishing attacks. that way, if something goes wrong with your device, you’ll know that you’ll still have access to all your important files and data. 15. block pop ups. Examples of phishing attacks. here’s an example of a phishing attempt that spoofs a notice from paypal, asking the recipient to click on the “confirm now” button. mousing over the button reveals the true url destination in the red rectangle. here’s another phishing attack image, this time claiming to be from amazon.
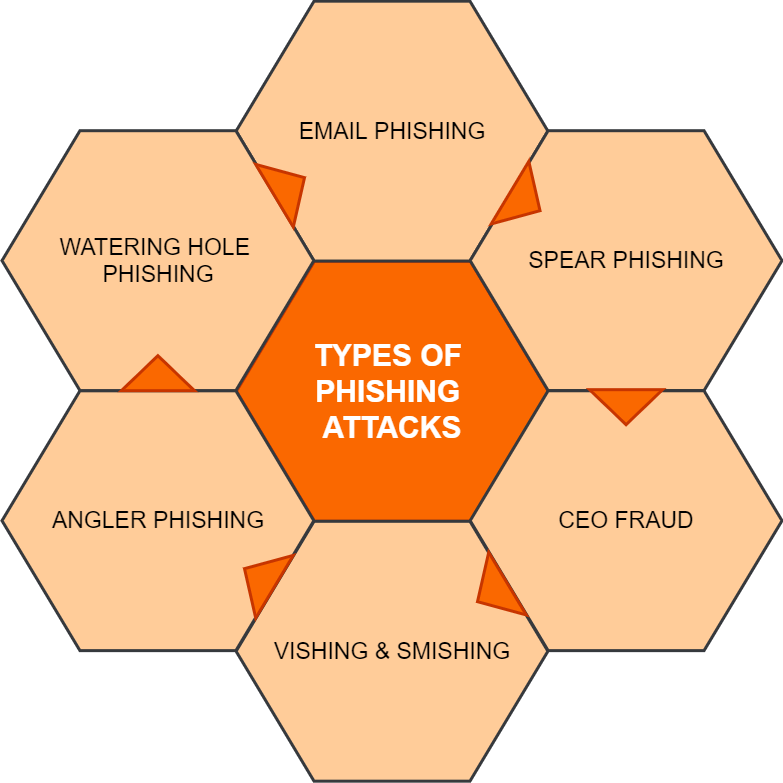
5 Common Types Of Phishing Attacks How To Recognize Avoid Them V Regularly back up your data. routinely backing up your data is a good way to increase your peace of mind and help protect against the damage of phishing attacks. that way, if something goes wrong with your device, you’ll know that you’ll still have access to all your important files and data. 15. block pop ups. Examples of phishing attacks. here’s an example of a phishing attempt that spoofs a notice from paypal, asking the recipient to click on the “confirm now” button. mousing over the button reveals the true url destination in the red rectangle. here’s another phishing attack image, this time claiming to be from amazon.

Comments are closed.